Must-Know Logs for SOC Analysts : First-Response Checklist for Triage, Threat Hunting & Incident Investigation
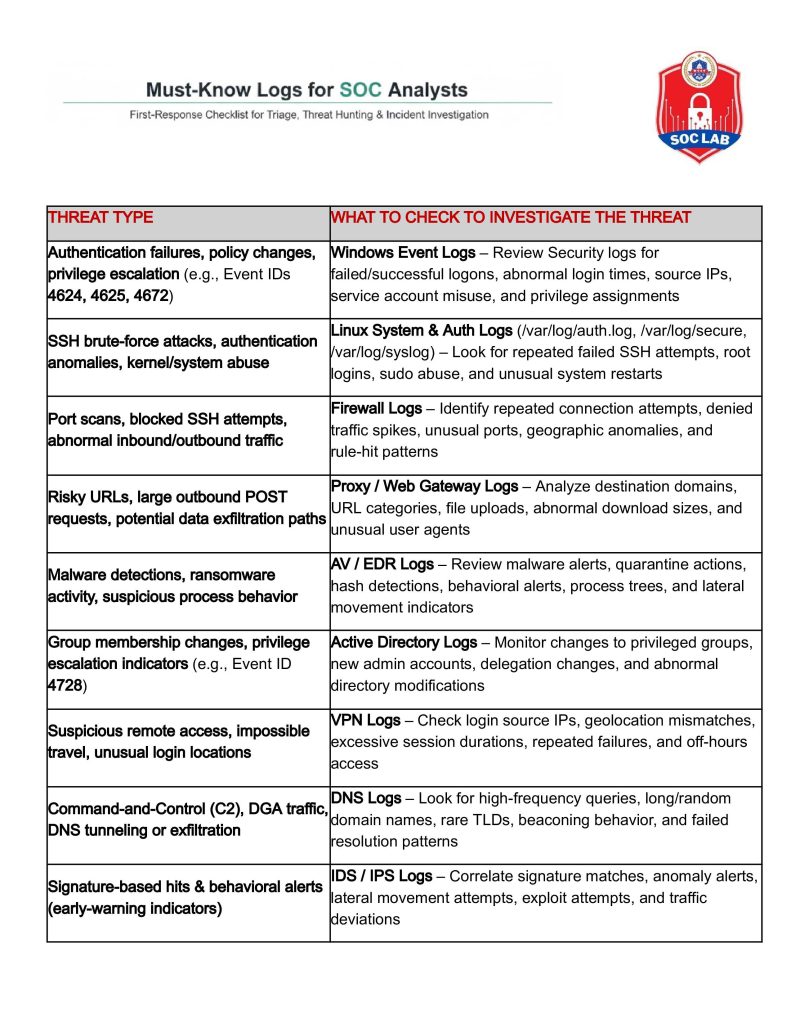
When an alert fires, the fastest path to clarity is knowing which log answers which question. Use this first-response checklist to guide triage, threat hunting, and incident investigation.
- Threat type: Authentication failures, policy changes, privilege escalation (e.g., Event IDs 4624, 4625, 4672)
What to check to investigate the threat: Windows Event Logs – Review Security logs for failed/successful logons, abnormal login times, source IPs, service account misuse, and privilege assignments
- Threat type: SSH brute-force attacks, authentication anomalies, kernel/system abuse
What to check to investigate the threat: Linux System & Auth Logs (/var/log/auth.log, /var/log/secure, /var/log/syslog) – Look for repeated failed SSH attempts, root logins, sudo abuse, and unusual system restarts
- Threat type: Port scans, blocked SSH attempts, abnormal inbound/outbound traffic
What to check to investigate the threat: Firewall Logs – Identify repeated connection attempts, denied traffic spikes, unusual ports, geographic anomalies, and rule-hit patterns
- Threat type: Risky URLs, large outbound POST requests, potential data exfiltration paths
What to check to investigate the threat: Proxy / Web Gateway Logs – Analyze destination domains, URL categories, file uploads, abnormal download sizes, and unusual user agents
- Threat type: Malware detections, ransomware activity, suspicious process behavior
What to check to investigate the threat: AV / EDR Logs – Review malware alerts, quarantine actions, hash detections, behavioral alerts, process trees, and lateral movement indicators
- Threat type: Group membership changes, privilege escalation indicators (e.g., Event ID 4728)
What to check to investigate the threat: Active Directory Logs – Monitor changes to privileged groups, new admin accounts, delegation changes, and abnormal directory modifications
- Threat type: Suspicious remote access, impossible travel, unusual login locations
What to check to investigate the threat: VPN Logs – Check login source IPs, geolocation mismatches, excessive session durations, repeated failures, and off-hours access
- Threat type: Command-and-Control (C2), DGA traffic, DNS tunneling or exfiltration
What to check to investigate the threat: DNS Logs – Look for high-frequency queries, long/random domain names, rare TLDs, beaconing behavior, and failed resolution patterns
- Threat type: Signature-based hits & behavioral alerts (early-warning indicators)
What to check to investigate the threat: IDS / IPS Logs – Correlate signature matches, anomaly alerts, lateral movement attempts, exploit attempts, and traffic deviations
